How to fix hacked Joomla Website and remove Malware?

Joomla is one of the most popular CMSs, known for its robust security features. However, no website is completely immune to hacking. Despite the best efforts made by the developers and community, there may be some unknown loopholes or zero-day exploits.
Some of the common vulnerabilities in Joomla includes:
- Cross-Site Scripting (XSS)
- Code Injection
- SQL Injection
Weak default admin passwords and outdated Joomla core systems or extensions can also make the site prone to cyberattacks.
In addition, a Joomla website can be compromised in several ways. Common threats include insecure server hosting, unsafe extensions due to Joomla’s open architecture, and phishing attacks.
Is your Joomla site hacked?
How do you know if your site is compromised or attacked by malware?
Let’s understand the symptoms of a hacked Joomla website and the steps to repair it.
How to know if your Joomla site is hacked?
Regular malware scans on your Joomla website can detect early hacking attempts.
If you don't scan, unexpected changes on web pages, like unfamiliar messages or links, might appear.
Other signs of a hack might be unknown redirects, or sudden ads and images.
You might also face automatic logouts, see new admin names, or experience slow page loading.
A sudden increase in website traffic is another red flag to watch out for.
Don't underestimate these symptoms. They can harm your business significantly.
For instance, they can affect your ranking on Search Engine Results Pages (SERPs).
Search engines like Google prioritize website safety. A detected hack can result in a warning and a lowered ranking.
A compromised website can damage your SEO and tarnish your site's reputation. Moreover, customer or user information could be at risk.
Hacks, like cross-site scripting, can redirect visitors to unwanted locations, leading to lost trust.
Lets list out some of the symptoms of Joomla website being hacked -
- Unexpected Web Page Changes: You may notice unfamiliar messages, links, images, or ads that you didn't place on your web pages.
- Redirection: Your website might redirect to unknown or suspicious websites.
- Automatic Logout: You may find yourself being logged out of your admin account automatically.
- New Admin Names: New administrator names that you didn't create may appear in your user list.
- Traffic Spikes: There might be an unexpected increase in website traffic.
- Slow Page Loading: Your website may load slower than usual.
- Altered SEO Settings: Changes in your SEO settings or metadata that you didn't make.
- Unusual Server Logs: You may notice unusual activities in your server logs.
- Email Spam: Your website starts sending out spam emails.
- Disabled Site: Your website or parts of it are unexpectedly disabled or not functioning correctly.
- Modified .htaccess: Using the FTP check the .htaccess file which is in the root folder. Check if any extra codes have been added to it.
How can you use Google as a security tool?
Google Search Console (GSC) (formerly Google Webmaster Tools) is a great tool for website owners. It can notify you if your website has been hacked or if malware has been detected.
Google's web crawlers constantly scan websites for various factors, including security issues. If they detect any signs of hacking or malware on your website, Google will send you an email alert via the GSC. These alerts can help you take immediate action to resolve the issue and protect your website.
In addition to security alerts, GSC provides insights about your website's performance.
It offers details on search traffic, usability issues, and can guide your SEO strategy.
Using GSC in your routine ensures a secure and high-performing website.
Another detection method: search your website on Google. A warning below the URL confirms malware presence.
Such warnings lead to drops in organic search traffic.
Google flags harmful sites, deterring visitors and lowering rankings.
One client's site was hacked due to an outdated Joomla plugin, leading to serious harm.
The hacker modified a JavaScript file, adding a suspicious link, damaging the site's reputation.
Pro Tip : Not just scan the PHP files but also the Javascript files. Most of the scan tools ignores scanning JS files or just searches for Base64, encode, decode keywords in the scripts. This doesn't help actually. Just go for a manual scan of the JS file.
So my Joomla website has been hacked. What now?
You have two options: hire a service that will do the Joomla malware removal for the right price, or do it yourself. If you're a DIY fan, make a jar of coffee ☕ and get ready for some serious cleaning work by following the steps below.
Backup the website
Make a full backup. This backup will contain malware traces, but if you need to find files or content that are not available elsewhere, you should save them in a quarantine folder on your local computer anyway.
Scan and Identify the hack
Scan Joomla site to identify malware locations and malicious payloads. For this, you can use the following tools
- SiteCheck
- VirusTotal: Its a great tool which analyses your website through 50+ security tools and generates a report for free.
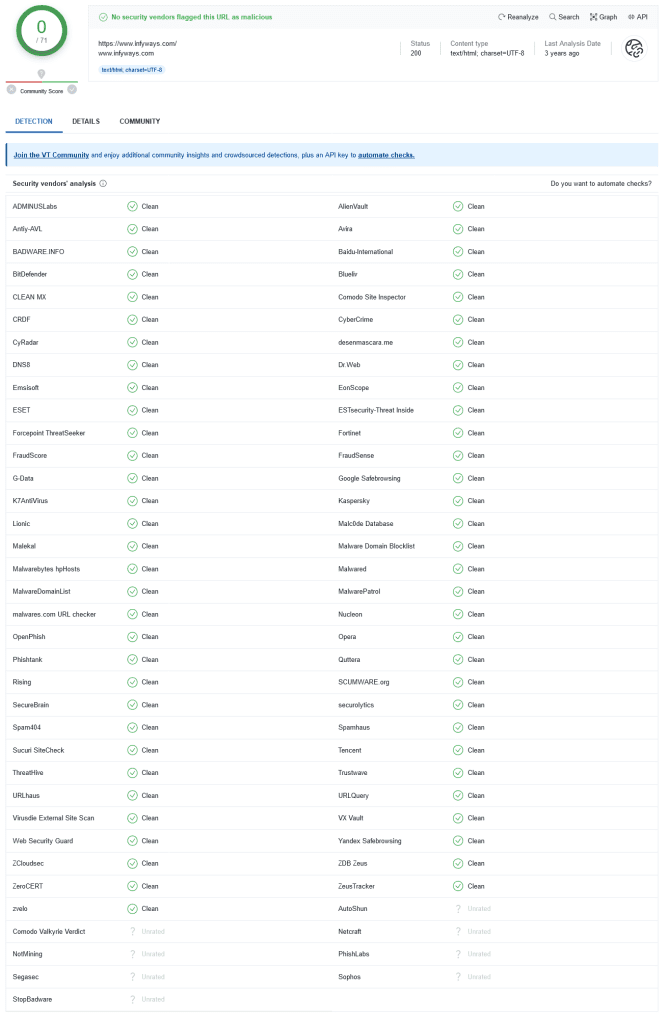
You can also use local antivirus software to detect infected files in the backup copy created in step 1. If the antivirus software detects infected files, they should be deleted from the backup and the host.
If your Joomla website seems to have been blacklisted by Google or other website security agencies, you can check the security status of Joomla. The website uses its diagnostic tool. To check Google’s transparency, visit the "Safe Browsing Site Status" website, where you can check
- Site security details, which provides information about malicious redirects, spam and downloads.
- Test details, which provide information about the latest Google scan that found the malware.
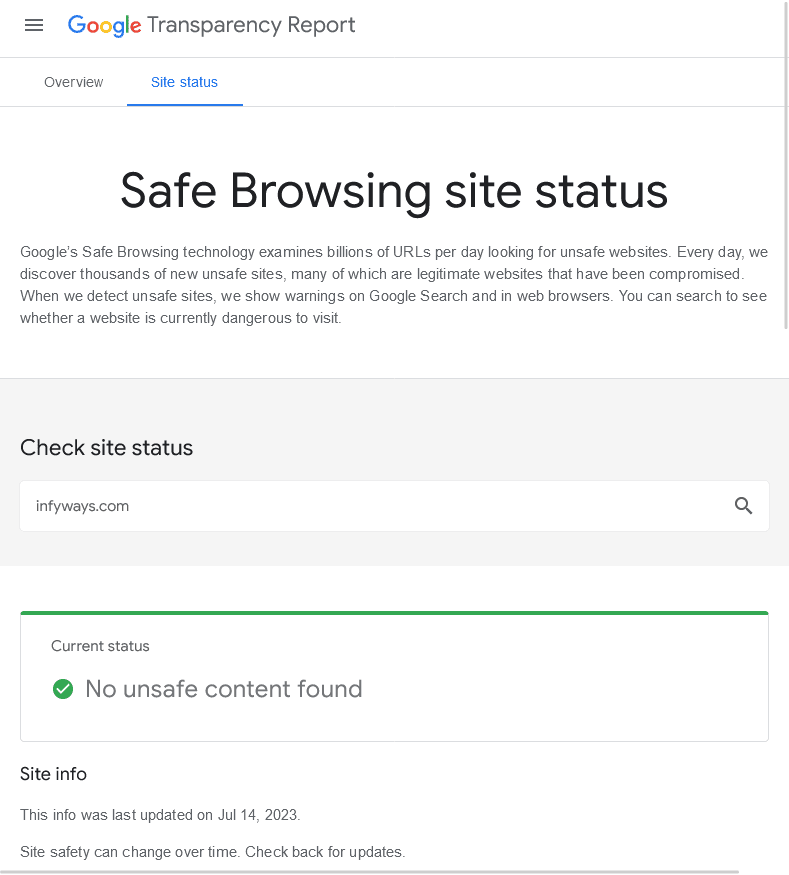
Use free security monitoring tools, such as Google Webmasters Central, Bing Webmaster Tools and Norton SafeWeb to check website security reports.
You can also check modified files manually. Using FTP you can browse the directory structure to find malicious files and delete them. In particular, check whether there are malicious files disguised as legitimate files in folders such as /tmp, /cache or /images-several common examples: test.html, tests.php, contacts.php, cron.css, css.php.
Fixing the Hacked Website
Gather Information: Find out where potential malware is, who's affected, and assess the threat.
Clean Up Site: Choose a full site cleanup. Compare infected files with old backups to see what's changed. Remove any harmful alterations.
Clean Database: Use a database management panel like PHPMyAdmin, or tools like Search-Replace-DB or Adminer, to clean the compromised Joomla database.
Secure User Accounts: This is crucial as hackers often leave backdoors for future access, even after a cleanup.
Remove Backdoors: These are typically in files that seem legitimate but are in the wrong directory. Complete removal is necessary to avoid re-infection.
Remember, these steps are key to repairing a hacked Joomla site and improving its Google ranking.
Clean up Hacked database tables
To remove the malware infection from your Joomla! Database, you need to open a database management panel, such as PHPMyAdmin. You can also use tools like Search-Replace-DB or Adminer.
First, start cleaning the infected database. Joomla SQL injection can create new database users. To find new users created after a certain date, use the following code:
Select * from users as u AND u.created > UNIX_TIMESTAMP(STR_TO_DATE('My_Date', '%M %d %Y '));Once a rogue user is found. Therefore, use the SQL statement Drop User to delete them;
To manually remove malware infections from Joomla! Database Table:
- Log in to the database management panel.
- Before making changes, back up the database.
- Search for suspicious content (for example, spam keywords, links).
- Open the table with suspicious content.
- Manually delete all suspicious content.
- Test to confirm that the site can still function normally after the change.
- Delete any database access tools you may have uploaded.
You can search your Joomla manually! Database, used for common malicious PHP functions, such as eval, base64_decode, gzinflate, preg_replace, str_replace, etc. Please note that Joomla also uses these features! Extensions are for good reasons, so make sure you test changes or get help to avoid accidentally breaking your site.
Secure the server
If the hosting provider detects a malware infection on a website, it may temporarily suspend your website to prevent it from infecting other websites hosted on the same shared server.
Even if the installation is safe, a malfunctioning server can also lead to Joomla hacking. Although there are many Joomla security issues. Some key points to remember are:
- Close all open ports.
- Delete unused subdomains.
- Regularly check for configuration issues.
- If you want to share the server, perform subnetting. Or use VPN.
- Prevent error messages from leaking information.
- Provide strong and random passwords for FTP accounts and databases!
- Make sure to use a firewall or some kind of security solution.
Fix file permissions
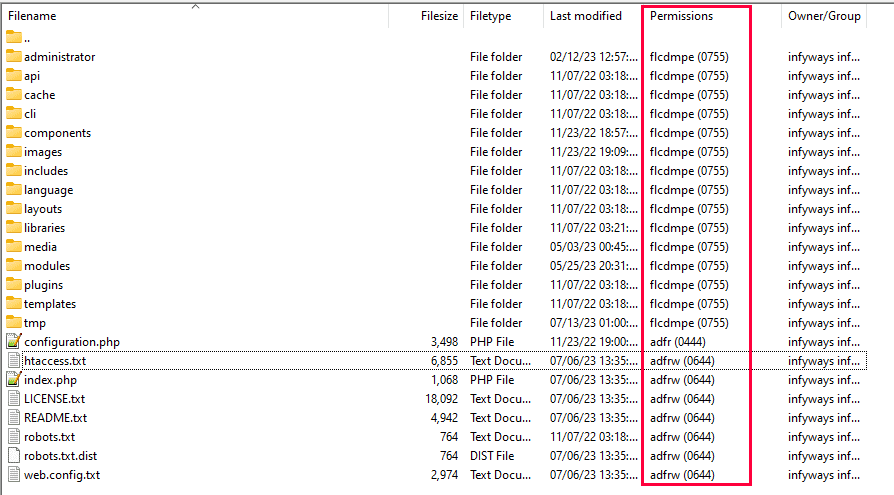
- First of all, please make sure that no user can upload executable files such as .php, .aspx, etc. Only image files can be uploaded to the server.
- Now proceed to set the file permissions of the server. Probably the most sensitive file is the .htaccess file. Therefore, appropriate file permissions must be set. Set your .htaccess permissions to 444 (r–r–r–) or 440 (r–r––).
- Also, please make sure that your PHP files will not be overwritten. Therefore, you need to set *.php to 444 (r–r–r–).
- The most important thing is to use popular Joomla extensions. Joomla is a fairly large CMS and popular extensions are more quickly updated in the event of vulnerabilities.
Check Hacked or Modified Files
If any scan or diagnostic page shows malicious domains or payloads, you can start by looking for those files on Joomla! Network Server. By comparing the infected files with known normal files (from official sources or reliable clean backups), you can identify and delete malicious changes.
To manually remove the malware infection from your Joomla! file:
- Log in to the server via SFTP or SSH.
- Before making changes, create a backup of the site files.
- Search your files to refer to the malicious domain or payload you pointed out.
- Identify the recently changed files and verify that they are legal.
- View files marked by the diff command during the core file integrity check.
- Use clean backups or official sources to restore or compare suspicious files.
- Remove any suspicious or unfamiliar code from your custom file.
- Test to confirm that the site can still function normally after the change.
Consider that the code may be confused or obscured by functions such as base64_decode, gzinflate, eval or other regular expression related functions. You can use a PHP decoder or online service to analyze the obfuscated code to reveal its actual function.
There is another quick way to find the modified files by using diff command in terminal.This can be used for comparison. To use the SSH command to check the integrity of the core file, do the following:
$ mkdir joomla$ cd joomla
First, we created a directory called joomla and switched to that directory.
$ wget https://github.com/joomla/joomla-cms/releases/download/3.9.22/Joomla_3.9.22-Stable-Full_Package.zip
$ tar -zxvf Joomla_3.9.22-Stable-Full_Package.zip
The wget command downloaded the Joomla file from GitHub. Second line of code then extract them.$ diff -r joomla-3.9.22 ./public_html
Finally, the diff command here is comparing content. This time we are looking for In the public_html file. Similarly, you can check multiple files. Moreover, the file It can be checked manually. Just use any FTP client to log in and check the files. SSH protocol Allows you to list file modifications.$ find ./ -type f -mtime -15
The SSH command here shows the files modified in the last 15 days. Similarly, you can change the time stamp. Please note if there are any recently modified files!
Check user Logs
The system log is the best tool to identify the cause of a Joomla hack. The system log records all previous activities. Therefore, whenever XSS or SQL injection is performed, there will always be a request record. In addition, hackers often create new administrator accounts. If you wish to check any suspicious users, then:
- Log in to your Joomla! Administrator area.
- Click User on the menu item, and then select Manage.
- Check the list, especially the list with the most recent registration date.
- Delete all unfamiliar users created by hackers.
- Check the last access date of legitimate users.
- Confirm all users who logged in at the suspicious time.
- If you know where the server logs are stored and how to search for requests to the Joomla administrator area, you can also parse the server logs!
- Users who log in at unusual times or geographic locations may have been compromised.
- If you see users logging from unknown IP address, remove them.
Post Hack Security
Update the Joomla Core, templates and Extensions
Most of the time a Joomla hack takes place due to unpatched files. Hence, the first step to follow post cleaning the hack is a Joomla Upgrade. Upgrades essentially remove vulnerable extensions and fill in security holes thus providing you with a secure environment.
Currently, the Joomla version 4.3.x is the most stable major version. Those using 1.5.x, 1.6.x, 1.7.x and 2.5.x branches should immediately switch to 4.3.x.
Other than major version update, also update all Joomla core files, components, templates, modules, and plugins.
Reset the credentials
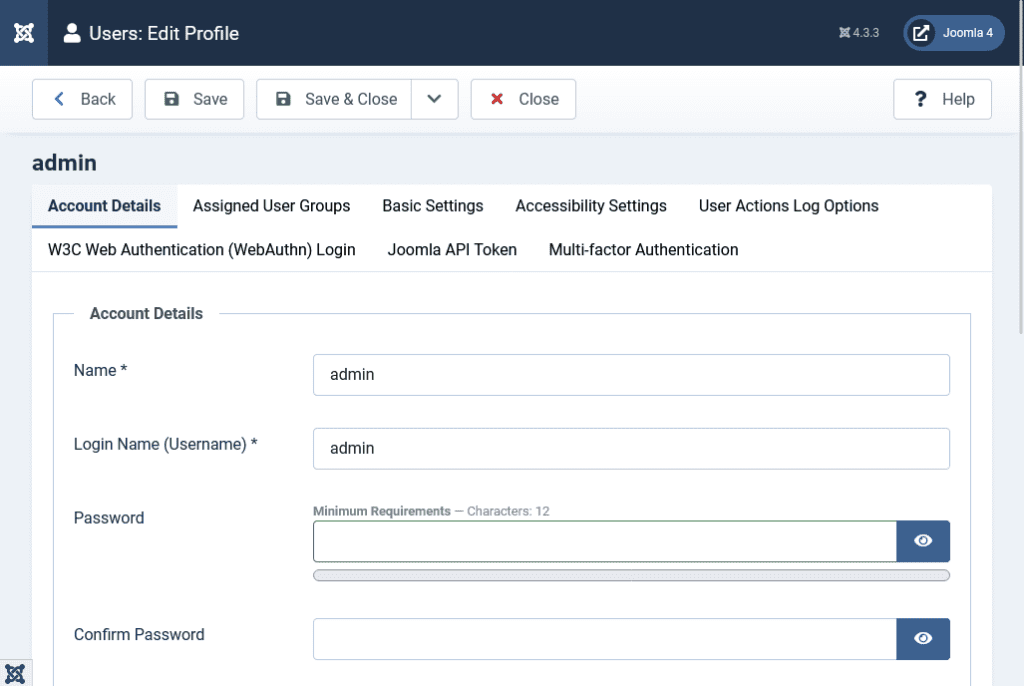
You should reset all Superuser Username and Password. Use an unique strong password to avoid re-infection.
- Log in to your Joomla! website.
- Click the User menu item. Open each user account.
- Change user password.
- Repeat this for every Superuser on your website.
You should reduce the number of administrator and super administrator accounts for all website systems. Implement the concept of least privilege. Give people only the access they need to get the job done.
Reinstall of Extensions
After hacking, it is also recommended to reinstall all extensions to ensure that they function properly and there is no residual malware. In addition, delete deactivated/deactivated templates, components, modules or plugins from the web server.
Sometimes, we forget to delete files related to these obsolete modules and plugins, which may still leave loopholes. Therefore, make sure to delete these files as well, as they may contain serious vulnerabilities.
After cleaning the hacked Joomla website, please make a backup. A good backup strategy is at the core of best security practices. Store the backup in a remote location, because storing the backup on the server may also lead to hacking.
Backup the website
The backup acts as a safety net. Now that your Joomla website is clean and you have taken some important post-hacking steps, please make a backup! Having a good backup strategy is the core of a good security posture.
Regular backup of files and database archives can avoid any trouble. Some extensions such as Akeeba Backup provide automatically scheduled backups that can be restored in the future if data is lost due to hacking. Learn how to backup Joomla.
Post Hack Security Tips or Joomla Hack Protection
Implementing the following security measures will protect your Joomla website from most attacks:
Avoid using weak passwords

Weak credentials may eventually leak through brute force vulnerabilities and act as common security vulnerabilities, resulting in compromised security. The easy-to-guess password and the default administrator account make it easier for Hackers to illegally access your Joomla website, thereby exposing a series of malicious activities. Long passwords with multiple characters are more secure than short passwords.
Restrict Access to Admin Panel
Hackers often resort to brute force attacks on easy-to-guess administrator login pages. Therefore, access to the administrator area must be restricted. It is recommended not to use the default administrator login page URL, but to replace it with a specific name.
Default Joomla URL
https://www.yourwebsite.com/administrator
URL after using a security plugin like RSFirewall/ Admin Tools
https://www.yourwebsite.com/administrator?secrectText
or
https://www.yourwebsite.com/secretText
This will be very difficult for a hacker to guess the administrator URL.
In addition, the management panel must be password protected. Admin tools by Akeeba, RSFirewall and other extensions allow Joomla site owners to change their login page URL. This can be a way to prevent Joomla administrator hack.
Use Security Extensions
Using security extensions is very helpful for protecting your Joomla website. These extensions, when properly configured for your site, can prevent any form of malicious activity and cover up security holes.
The extension allows you to prevent hacker attacks and close the security holes of the Joomla website.
Use Two Factor Authentication
A two-step verification code (commonly called a one-time password: OPT) makes your Joomla website more secure.
Even if your password is guessed or leaked, you must still pass the authentication code to illegally access your account.
Never use Nulled templates or extensions 🚫
Never download premium extensions, plugins or any items for free from unauthenticated or unofficial sources.
Extensions and templates from unknown sources may be corrupted or contain malware, which may harm your website. Don't think about saving money here, but spend on authentic sources.
Use SSL Certification
Whenever a user logs into the site, his/her credentials will be sent to the server (no encryption). By using SSL certificates, these credentials will be encrypted before being sent to the server. In this way, SSL certification can provide additional protection for your Joomla website.
You can use LetsEncrypt SSL for free.
File Permission
Always manage permissions to files and directories, and never grant full access to permissions 777. Never grant full access or authority to 777, but use 755 for folders, 644 for files, and 444 for configuration.php files.
Update Regularly
Last but not the least, a secure Joomla website is a website that is updated regularly. Each version update has released security enhancements and bug fixes.
An outdated version of Joomla or any other outdated extensions/plugins can sneak into hackers.
If your website was hacked long before it was cleaned up, it is likely to be blacklisted. This means that it will not appear in search results to protect users from potential malware infections, so you will not have other visitors and you will lose confidence.
Even if you completely clean up your website, it will continue to be blacklisted for several days.
Request a Review to Google
https://youtu.be/lc3UjnDcMxoIn order to speed up the process, once your website is clean and healthy, please use Google’s Search Console for review. Google will scan your website and if no malware infection is found, it will stop displaying warning messages next to your website’s metadata.
But you will have to wait a few days until this happens. Using Search Console, you can also access the URL removal tool to request that all URLs added by malicious hands be removed from the Google index.
After cleaning the website, please take necessary measures to prevent future attacks, such as scanning your website regularly to check for malware infection.
Joomla Hack Fixing Services
The steps listed above can provide you with a DIY guide to recover your website from a hacker attack. However, if you do not have the time or confidence in yourself to complete the work, you can hire an expert to repair the hacked Joomla website.
This will cost you, but the time saved may be worth it. Remember, your website is offline every minute -Or worse, losing your reputation online-may mean you have lost dollars.
You can hire professionals to do it.
Yes, you can hire us and we will fix your website within a few hours. You can contact us and we will contact you as soon as possible.
Conclusion
If you have a good recent backup and you can more easily repair the website hacked by Joomla, you can avoid half of the headache. It insists on regular backups, because not only hacker attacks, but also a lot of data lost even during website crashes. This proves the importance of regular and tested backups.
All modifications made after the last known backup will be lost. Therefore, these backups must be performed frequently, because you never know when your website will be hacked.
Fixing your hacked Joomla website will cost you money or time. But don’t think you’re wasting money, but treat it as an investment in enhancing the security of your website. After repairing and protecting it, your website will receive strong support, and your customers or visitors will trust you and your business more. Chat with our security expert now!




